A Brief Description of Ransomware Attacks
My submission for IE4758 Information Security 2022 Assignment
"It has been reported that the number of ransomware attacks have significantly increased as many people are still working from home and the number of online users has significantly increased. Thus, the purpose of this assignment is to research and highlight how cyber criminals are launching ransomware attacks and how businesses, governments and individuals are developing policies and are using technology for protection."
Ransomware attacks have been on the rise amid the global pandemic. Part of the reason being that more people are online for both work and leisure. The demand for internet services has increased to reflect this change in lifestyle. While the convenience of online services benefits us in carrying out our daily activities, malicious actors are capturing this opportunity to target governments, businesses as well as individuals to profit from the lack of information security. It has been reported that in Singapore, about 1.16 million US dollars have been paid out on average to ransomware attackers in the year of 2021.1 This puts Singapore at the 6^th^ place in the chart of countries with highest average ransom payments. Across the globe, companies have also fallen prey to ransomware attacks. JBS, the world's largest meat packer, halted its operations in North America and Australia due to suspension of cyber systems that were attacked.2 The ramifications of ransomware attacks highlight the importance of prevention and protection against the cyber criminals with effective security policies and best-practices.
Elements of ransomware attacks
Overview
Ransomware is a term to describe ransom malware, which is a type of malware that prevents users from accessing their system or personal files. The attackers then demand ransom payment in exchange for the data. The ransom is typically paid in Bitcoins or other cryptocurrencies to reduce traceability. Despite payment, it is worth noting that there is no guarantee that the hackers will return or decrypt the data.
Types of ransomware
In general, there are three types of ransomwares: Crypto ransomware, Locker ransomware, and Scareware.
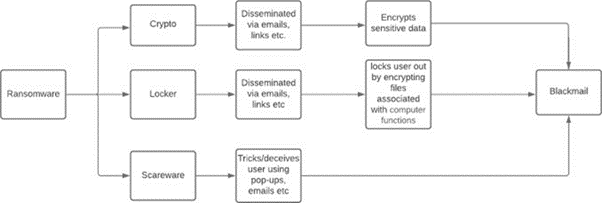
Fig1 Types of ransomware3
How cyber criminals are launching ransomware attacks
To launch ransomware attacks, cyber criminals typically perform the following:
Creating ransomware
Besides developing custom and novel ransomware, novice cyber criminals are also able to launch attacks with easily obtainable ransomware toolkits and via RaaS (ransomware as a service). RaaS allows ransomware developers to generate variations of an existing ransomware and sell it for a profit.
Distributing ransomware
Most ransomwares are distributed through phishing via emails or deceptive links on vulnerable websites. The target group unknowingly opens an attachment or clicks on a hyperlink that results in the download of malicious software. Such software then requests for execution permission (or exploits existing vulnerabilities) and proceeds with harmful activities in the computing devices.
Setting up command and control servers
Some ransomware will require external servers that they use to store encryption/decryption keys and look up dynamic pricing according to the IP address of the infected machine.
Receive payment and decryption process
After a ransomware has encrypted files or blocked system functionalities, it typically reveals an instruction to notify the user on the attack and how payment is expected. Such instructions would include steps to purchase Bitcoin and describe how decryption can be done.
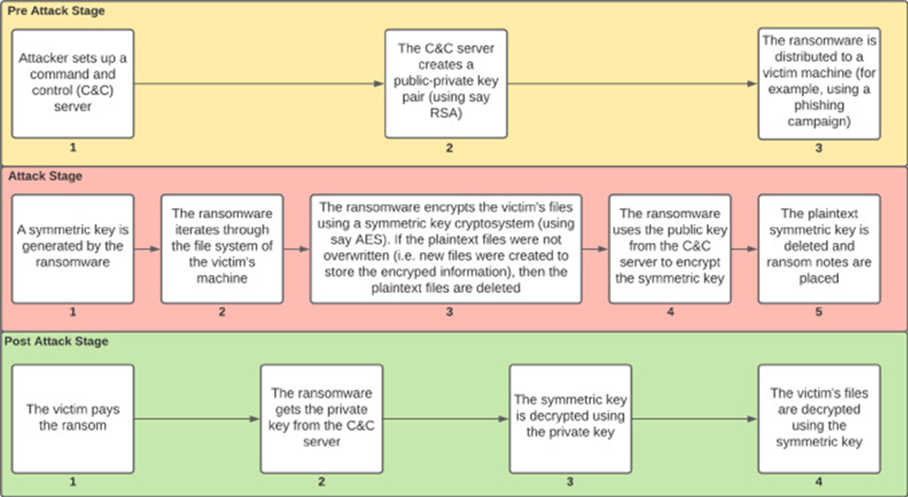
Fig2. Hybrid approach to encrypt and decrypt a user's data4
Defence against ransomware attacks
How are governments, businesses, and individuals affected by ransomware
While all parties that are hit by ransomware encounter destruction to their digital information and private data, ransomware criminals have differentiated approaches to deal with different groups of victims. While the criminals demand payment to recover data, businesses and governments are generally required to pay a larger sum due to their ability to pay and the urgency to continue operation. Businesses also have a huge interest in protecting their reputation should the cyber criminals threaten to release the encrypted data online. As for governments, they typically hold more sensitive personal data which may have a wide impact if breached.
Defence against ransomware attacks generally involve a combination of policy and technology. While technical advances in anti-virus and ransomware research can help make machines less vulnerable to ransomware attacks, human actions are often the weak point of the system. In addition to prevention, policies are also important should the event of a ransomware attack happen. A response checklist will be effective when dealing and recovering from a ransomware attack.
Prevention
To prevent ransomware attacks requires both hardware protections and human intervention.
Secure data and devices
Since files are typically under attack by ransomware, it is important to maintain offline, encrypted backups of data. For cloud infrastructures, it may also be useful to maintain an image of critical systems for rebuilding them in the event of compromise. A periodic schedule should be created to patch bugs and known vulnerabilities.5 In addition, anti-virus and network firewalls should be installed and updated to filter out potentially harmful network requests.
Education
By providing training and workshops to share best practices, we will be less likely to fall for phishing attacks and naively bring ransomware into the system. Education about cyber security can also highlight high risk activities such as downloading unverified email attachments and executing malicious macros hidden in Excel spreadsheets. Other measures such as improving password security and understanding configurations and system settings may also go a long way to help keep attackers out of the system.
Drills and insurance
Safety drills may be helpful for governments and businesses to detect potential loopholes in the current defence system, by simulating an attack and analyse the response. In addition, Cyber insurance can provide coverage against ransomware. In the state of ransomware 2022 report6, 89% of those hit by ransomware have cyber insurance.
Response
As it is difficult to prevent ransomware attacks due to resource constraints and human errors, a proper response plan is required to actively react to the attacks. This involves setting up cybersecurity budgets and an incident response plan. The plan may include details such as immediate response by investigating and isolating affected servers and machines to reduce further damage, engaging in negotiation with the cyber criminals, recovering loss of assets from backups and setting up temporary alternatives that are required to maintain business operations.
Recovery
Recovery from ransomware attacks is a continued effort from the active response to prevent future attacks. This means engaging law enforcement and cyber security firms to evaluate, analyse, and rebuild the system to mitigate security risks.7 While paying the cyber criminals could be cost-effective, it is largely an undesirable solution as it funds the cyber criminals further and may not always guarantee the return of the digital assets.
Challenges and advancements
With more information online and the recent advances in blockchain based technology, we may need to caution ourselves against block-chain based ransomware8 schemes that could use smart contracts to automate and attack with a more irreversible effect.
While ransomwares have grown to be a billion-dollar business, research on how to identify and protect against them also improved over the years. Besides a signature-based detection that may be inadequate, machine learning approaches9 have been applied to train and then spot ransomware accurately.
Conclusion
The battle against ransomware attacks is an arduous and relentless one. As humans further integrate their lives into the digital world, the attack vectors continue to increase over the years. Hence, education about information security and vigilance in carrying out measures to safeguard ourselves against attacks will continue to be necessary and important in keeping our information safe and secure.
Citations
-
Andronio, N., Zanero, S., & Maggi, F. (2015, November). Heldroid: Dissecting and detecting mobile ransomware. In international symposium on recent advances in intrusion detection (pp. 382-404). Springer, Cham.
-
Al-rimy, B. A. S., Maarof, M. A., Prasetyo, Y. A., Shaid, S. Z. M., & Ariffin, A. F. M. (2018). Zero-day aware decision fusion-based model for crypto-ransomware early detection. International Journal of Integrated Engineering, 10(6).
-
Alshaikh, H., Ramadan, N., & Hefny, H. A. (2020). Ransomware prevention and mitigation techniques. Int J Comput Appl, 117, 31-39.
-
Aurangzeb, S., Aleem, M., Iqbal, M. A., & Islam, M. A. (2017). Ransomware: a survey and trends. Journal of Information Assurance & Security, 6(2), 48-58.
-
Delgado-Mohatar, O., Sierra-Cámara, J. M., & Anguiano, E. (2020). Blockchain-based semi-autonomous ransomware. Future Generation Computer Systems, 112, 589-603.
-
Low, D. (2022, August 30). Ransomware attacks threaten nations, 137 s'pore firms fell prey in 2021: CSA. The Straits Times. Retrieved September 19, 2022, from https://str.sg/wD9K
-
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack 2017. International Journal of Advanced Research in Computer Science, 8(5), 1938-1940.
-
Ransomware guide. CISA. (n.d.). Retrieved September 27, 2022, from https://www.cisa.gov/stopransomware/ransomware-guide
-
Richardson, R., & North, M. M. (2017). Ransomware: Evolution, mitigation and prevention. International Management Review, 13(1), 10.
-
Rosenberg, J. M. (2015, April 8). A Q&A about the malicious software known as ransomware. Retrieved April 8, 2015, from http://www.salon.com/2015/04/08/a_qa_about_the_malicious_software_known_as_ransomware/
-
The state of ransomware 2022 - sophos. (n.d.). Retrieved September 27, 2022, from https://assets.sophos.com/X24WTUEQ/at/4zpw59pnkpxxnhfhgj9bxgj9/sophos-state-of-ransomware-2022-wp.pdf
-
US says ransomware attack on Meatpacker JBS likely from Russia; Cattle Slaughter resuming. The Straits Times. (2021, June 3). Retrieved September 19, 2022, from https://str.sg/3krC
-
Zetter, K. (2015, September 17). Hacker lexicon: A guide to Ransomware, the scary hack that's on the rise. Retrieved from Security, https://www.wired.com/2015/09/hacker-lexicon-guideransomware-scary-hack-thats-rise/
End
Footnotes
-
Low, D. (2022, August 30). Ransomware attacks threaten nations, 137 s'pore firms fell prey in 2021: CSA. The Straits Times. Retrieved September 19, 2022, from https://str.sg/wD9K ↩
-
US says ransomware attack on Meatpacker JBS likely from Russia; Cattle Slaughter resuming. The Straits Times. (2021, June 3). Retrieved September 19, 2022, from https://str.sg/3krC ↩
-
Andronio, N., Zanero, S., & Maggi, F. (2015, November). Heldroid: Dissecting and detecting mobile ransomware. In international symposium on recent advances in intrusion detection (pp. 382-404). Springer, Cham. ↩
-
Beaman, C., Barkworth, A., Akande, T. D., Hakak, S., & Khan, M. K. (2021). Ransomware: Recent advances, analysis, challenges and future research directions. Computers & Security, 111, 102490. https://doi.org/10.1016/j.cose.2021.102490 ↩
-
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack 2017. International Journal of Advanced Research in Computer Science, 8(5), 1938-1940. ↩
-
The state of ransomware 2022 - sophos. (n.d.). Retrieved September 27, 2022, from https://assets.sophos.com/X24WTUEQ/at/4zpw59pnkpxxnhfhgj9bxgj9/sophos-state-of-ransomware-2022-wp.pdf ↩
-
Richardson, R., & North, M. M. (2017). Ransomware: Evolution, mitigation and prevention. International Management Review, 13(1), 10. ↩
-
Delgado-Mohatar, O., Sierra-Cámara, J. M., & Anguiano, E. (2020). Blockchain-based semi-autonomous ransomware. Future Generation Computer Systems, 112, 589-603. ↩
-
Alshaikh, H., Ramadan, N., & Hefny, H. A. (2020). Ransomware prevention and mitigation techniques. Int J Comput Appl, 117, 31-39. ↩